本ページは広告が含まれています。気になる広告をクリック頂けますと、サーバ運営費になります(^^
ただ3か所で接続するだけでなく、IPSecで接続してきた先にあるサーバに接続できるように設定を変更していきたいと思います。
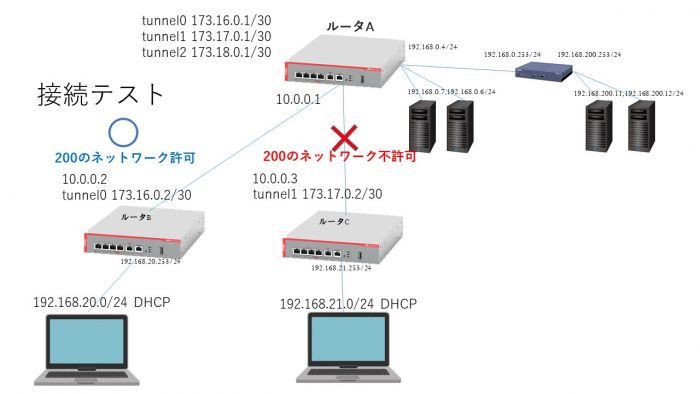
ルータA
ルータAは本社の位置づけにあるルータで、拠点間をIPSec通信で結んで本社サーバに接続します。受け側のルータというか、
! interface eth1 ip address 10.0.0.1/8 ! interface vlan1 ip address 192.168.0.4/24 ! !subnet 192.168.22 のネットワークは拡張 zone private network lan ip subnet 173.16.0.0/30 ip subnet 173.17.0.0/30 ip subnet 173.18.0.0/30 ip subnet 192.168.0.0/24 ip subnet 192.168.20.0/24 ip subnet 192.168.21.0/24 ip subnet 192.168.22.0/24 ip subnet 192.168.200.0/24 ! !host eth1のip addressは直接割り当てたIPアドレスを指定します zone public network wan ip subnet 0.0.0.0/0 interface eth1 host eth1 ip address 10.0.0.1 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.eth1 to public.wan rule 40 permit isakmp from public.wan to public.wan.eth1 rule 50 permit esp from public.wan.eth1 to public.wan rule 60 permit esp from public.wan to public.wan.eth1 protect ! nat rule 10 masq any from private to public enable ! crypto isakmp key secret-ab address 10.0.0.2 crypto isakmp key secret-ac address 10.0.0.3 ! interface tunnel0 ip address 173.16.0.1/30 tunnel source 10.0.0.1 tunnel destination 10.0.0.2 tunnel mode ipsec ipv4 tunnel protection ipsec ip tcp adjust-mss 1260 mtu 1300 ! interface tunnel1 ip address 173.17.0.1/30 tunnel source 10.0.0.1 tunnel destination 10.0.0.3 tunnel mode ipsec ipv4 tunnel protection ipsec ip tcp adjust-mss 1260 mtu 1300 ! !tunnel2は拡張 interface tunnel2 ip address 173.18.0.1/30 tunnel source 10.0.0.1 tunnel destination 10.0.0.4 tunnel mode ipsec ipv4 tunnel protection ipsec ip tcp adjust-mss 1260 mtu 1300 ! ip route 192.168.20.0/24 tunnel0 ip route 192.168.20.0/24 null 254 ip route 192.168.21.0/24 tunnel1 ip route 192.168.21.0/24 null 254 ip route 192.168.22.0/24 tunnel1 ip route 192.168.22.0/24 null 254 ip route 192.168.200.0/24 192.168.0.253 ! end
ルータB
ルータB配下のネットワークは本社ネットワークの
192.168.0.0/24
および、もっと深いところにあるサーバ
192.168.200.0/24
に接続できるようにします。
! interface eth1 ip address 10.0.0.2/8 ! interface vlan1 ip address 192.168.20.253/24 ! zone private network lan ip subnet 173.16.0.0/30 ip subnet 192.168.0.0/24 ip subnet 192.168.20.0/24 ! IPSecで直接ではないが、200のネットワークを追記しておく ip subnet 192.168.200.0/24 ! zone public network wan ip subnet 0.0.0.0/0 interface eth1 host eth1 ip address 10.0.0.2 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.eth1 to public.wan rule 40 permit isakmp from public.wan to public.wan.eth1 rule 50 permit esp from public.wan.eth1 to public.wan rule 60 permit esp from public.wan to public.wan.eth1 protect ! nat rule 10 masq any from private to public enable ! crypto isakmp key secret-ab address 10.0.0.1 ! interface tunnel0 ip address 173.16.0.2/30 tunnel source 10.0.0.2 tunnel destination 10.0.0.1 tunnel mode ipsec ipv4 tunnel protection ipsec ip tcp adjust-mss 1260 mtu 1300 ! ip route 192.168.0.0/24 tunnel0 ip route 192.168.0.0/24 null 254 ip route 192.168.200.0/24 tunnel0 ip route 192.168.200.0/24 null 254 ! end
ルータC
ルータC配下のネットワークからは、
192.168.0.0/24
のみアクセスできるようにする。
ルータC ! interface eth1 ip address 10.0.0.3/8 ! interface vlan1 ip address 192.168.21.253/24 ! zone private network lan ip subnet 173.17.0.0/30 ip subnet 192.168.0.0/24 ip subnet 192.168.21.0/24 ! zone public network wan ip subnet 0.0.0.0/0 interface eth1 host eth1 ip address 10.0.0.3 ! application esp protocol 50 ! application isakmp protocol udp sport 500 dport 500 ! firewall rule 10 permit any from private to private rule 20 permit any from private to public rule 30 permit isakmp from public.wan.eth1 to public.wan rule 40 permit isakmp from public.wan to public.wan.eth1 rule 50 permit esp from public.wan.eth1 to public.wan rule 60 permit esp from public.wan to public.wan.eth1 protect ! nat rule 10 masq any from private to public enable ! crypto isakmp key secret-ac address 10.0.0.1 ! interface tunnel1 ip address 173.17.0.2/30 tunnel source 10.0.0.3 tunnel destination 10.0.0.1 tunnel mode ipsec ipv4 tunnel protection ipsec ip tcp adjust-mss 1260 mtu 1300 ! ip route 192.168.0.0/24 tunnel1 ip route 192.168.0.0/24 null 254 ! end


